
Some consumer PCs also appear to have dangerous Intel exploit
 Image: Gordon Mah Ung
Image: Gordon Mah Ung
If you think you’re immune from a scary exploit found in Intel’s Active Management Technology just because you’re a consumer, think again.
The exploit, disclosed on May 1, lets bad actors bypass authentication in Intel’s remote management hardware to take over your PC. This hardware, built into enterprise-class PCs, lets IT administrators remotely manage fleets of computers—install patches and software, and even update the BIOS as though they were sitting in front of it. It is, in essence, a God-mode.
Here’s the fine print: Many early news reports said “consumer PCs are unaffected.” But what Intel actually said was, “consumer PCs with consumer firmware” are unaffected.
The problem is, plenty of consumers use business-class hardware—and not just the fringe who’ll buy or inherit commercial-class laptops and workstations. Many budget PCs use chipsets, firmware, and motherboards that were designed for small business machines. These machines may be exposed to the exploit through Intel’s Small Business Advantage technology, which is is a scaled-down version of AMT.
For example, some of Intel’s NUC computers feature Small Business Advantage support. Users testing their systems for the exploit have reported on forums such as Reddit that their consumer-focused H97-based boards have the exploit.
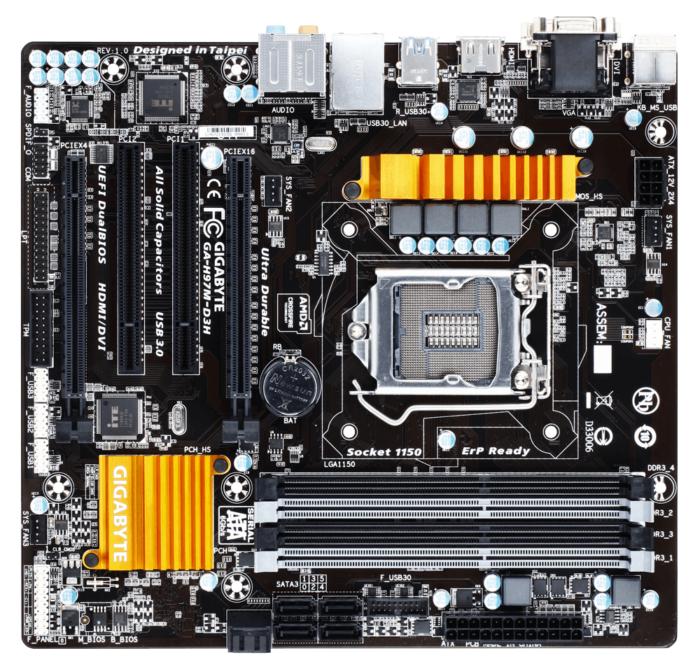 Gigabyte
GigabyteOne Reddit user reported that this Gigabyte H97M-D3H with a Core i5-4590 has the AMT exploit.
How to find out whether your PC is safe
While the vast majority of consumer PCs probably don’t have the exploit, it wouldn’t hurt to take five minutes to check your system.
First, download Intel’s tool to check for the vulnerability. You can also click this link to download it from Intel directly. It’s listed as supporting Windows 10 and Windows 7, but we had no issues running it on Windows 8.1.
Once you’ve downloaded it, decompress the zip file to a folder. Open the folder, then open its Windows subfolder. Inside you’ll find several files. Launch Intel-SA-00075-GUI.exe.
 IDG
IDGYou can quickly check for a critical security flaw on many corporate and small business PCs.
After a minute or less, the utility will spit out the results of the risk on your machine. Obviously, many corporate boxes have this dangerous exploit, such as this older Sandy Bridge corporate box we checked.
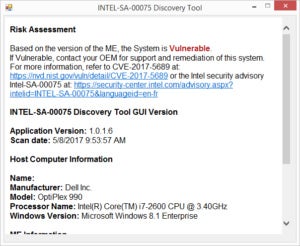 IDG
IDGMany business PCs are exposed to the Intel AMT exploit, as well as some PCs built using business-class components.
This new Dell XPS 15 consumer laptop, on the other hand, seems right as rain.
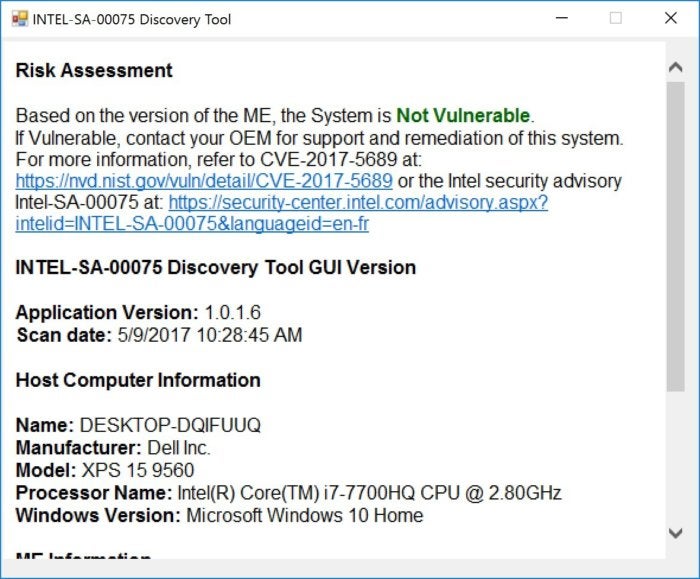 IDG
IDGA consumer Dell XPS 15 seems safe from the dangerous AMT exploit.
What to do if your PC has the exploit
If the utility results in a Vulnerable result, the next step is to check with your PC maker. Dell, HP, Lenovo, Fujitsu, and probably most major OEMs are already working on firmware fixes. If you run a DIY PC or a machine built by your local computer store, check with the motherboard vendor itself for firmware updates.
Gigabyte officials told PCWorld they are taking it seriously, and a fix is inbound.
“We were made aware of the issue from Intel and we are on track to update BIOS in 2 weeks,” said Gigabyte’s Alan Szeto. “Newer boards like Q270/Q170 are in first priority for the fixes with the older Q and B chipsets following. We know that older affected boards are still in use, so we will address the issue accordingly.”
If your PC is so old that you’re unlikely to get a firmware patch soon or at all, Intel has a “mitigation guide” that you can download. The guide has several detailed steps to help reduce your risk.
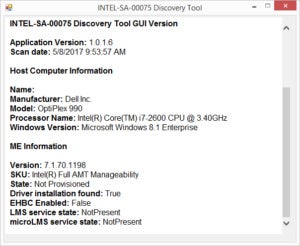 IDG
IDGEven thought this PC has the Intel AMT exploit vulnerability, some researchers think it would require the machine to be provisioned for remote support before an attack would succeed.
Is it really that dangerous?
A vulnerability that lets someone boot up your PC and install software at will, and even bypass logging in, sounds about as bad as it can get. Still, it’s not clear just how easy this is to exploit. Security reporter Dan Goodin of Arstechnica reported last week that some researchers believe the exploit would have to be present and the machine would have to be set up or provisioned for remote management for it to open to the attack. Goodin, however, followed up with a report on Saturday that researchers had bypassed the AMT without even entering a password.
In the end, the first step in fixing a problem is recognizing that you have one. If you think you might have the exploit on your machine, run the check.