
Usage for Tor doubles in wake of secure email shutdowns, arrival of the PirateBrowser
 Image: Tor
Image: Tor
The Tor anonymity network is enjoying a massive uptick in popularity after two significant privacy-minded events took place earlier this month
First, there were the sudden shutdowns of Lavabit and Silent Circle‘s Silent Mail, two secure email services that voluntarily closed their doors on Thursday, August 8, rather than allow the U.S. government access to their users’ messages.
On August 10, mere days after Lavabit and Silent Circle took one for the team, the popular Pirate Bay file-sharing site released its PirateBrowser, a web browser that allows users to hop onto the Tor network in order to circumvent government firewalls to access torrent sites and other banned parts of the Web.
By August 18, the number of users accessing the Tor network started creeping up, and it has only climbed higher and higher (and higher) since. Tor now regularly sees more than twice as many daily users as it did before the email shutdowns and the PirateBrowser’s release.
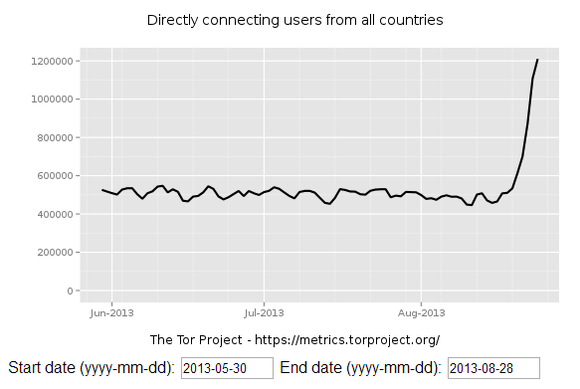 Tor Project
Tor ProjectDifferences between Tor browser and the PirateBrowser
While the PirateBrowser and standard Tor software both rely on the Tor network, they use it in very different ways.
Once you’ve installed Tor’s software on your PC—most often in the form of the Tor browser bundle—the service allows you to surf the web anonymously by encrypting your Internet connection requests and bouncing them between numerous “relay nodes” before finally sending them on to the final destination.
No node knows the identifiable information of any nodes in the chain aside from the ones they’re taking information from and passing information to and., just to be on the safe side, each hop along the way gets a whole new set of encryption keys.
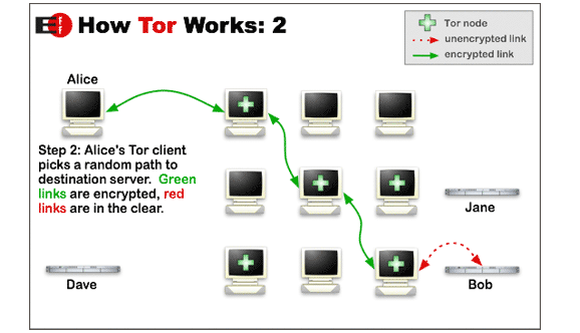
“The idea is similar to using a twisty, hard-to-follow route in order to throw off somebody who is tailing you—and then periodically erasing your footprints,” explains the Tor website. All the hip-hopping makes for a very secure (yet very slow) browsing experience, assuming you’re smart about your usage habits. It’s also great for bypassing government firewalls.
Tor’s “onion-routing” technology also enables the creation of “hidden services,” or websites that can also hide their server identity from its users and are only accessible while using Tor. This extreme level of anonymity makes the so-called “Onionland” darknet a haven—not only for seedy types, but also for people who want (or need) to stay anonymous, such as political dissidents and whistleblowers—the type of people who may have relied on Lavabit and Silent Mail previously.
[Now read: Meet the Darknet, the hidden, anonymous underbelly of the Web]
The PirateBrowser behaves a bit differently, however. From its website:
No, it’s not intended to be a TOR Browser, while it uses the Tor network, which is designed for anonymous surfing, this browser is ONLY intended to circumvent censorship. The Tor network is used [in the PirateBrowser] to help route around the censoring/blocking of websites your government doesn’t want you to know about.
To drive home the point that the PirateBrowser isn’t designed for anonymity, it doesn’t include the encryption-providing “HTTPS Everywhere” plugin found in the Tor Bundle.
Additionally, the PirateBrowser only accesses Tor when you’re using the browser to try to access a blocked website. Non-blocked websites are delivered to your browser normally, rather than hopping all around.
Anonymous messaging with Tor

While the drastic uptick in usage is probably mostly attributable to the PirateBrowser—the Pirate Bay’s custom browser was downloaded more than 100,000 times in a matter of days—the Lavabit and Silent Circle shutdowns likely also drove privacy-minded people further underground.
Tor itself isn’t an email provider, though—it’s just anonymizing routing technology, pure and simple. What’s more, the most popular Hidden Service email provider in Onionland, Tormail, was recently killed by the U.S. government. It was collateral damage in the takedown of a service provider hosting many of the Web’s child pornography sites.
That’s not to say Tor can’t be used to send secure messages online, however.
Signing in to a webmail account while using Tor will obviously give your identity away, but using Tor in conjunction with dummy email accounts and PGP encryption would deliver a relatively strong level of privacy. Privacy buffs can also take advantage of Onionland’s messaging services, which deliver a very high level of anonymity.
No matter what accounts for Tor’s dramatic spike in popularity, one thing’s for certain: More people than ever are turning to technology to spite Big Brother.
Via Reddit